
Secure and Intelligent Access Control for Devices, Users & Applications
Quantum Access Manager (QAM) is a unified access control platform designed to help organizations secure, authenticate and manage access to their networks, applications and devices across campuses, branches and remote environments.
From device enrollment and posture checks to certificate-based authentication and policy enforcement, QAM brings identity and access under one powerful console.
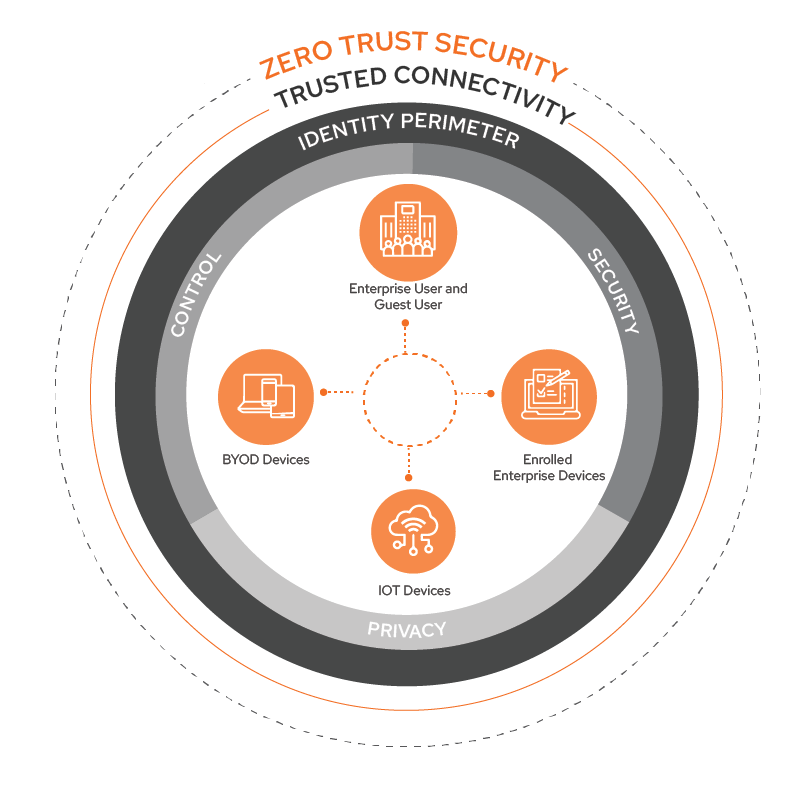
AAA Authentication with 802.1X
Centralized Authentication, Authorization and Accounting for Wi-Fi, wired, VPN and web-based access. Smoothly integrates with existing identity infrastructure such as AD, LDAP and SAML.
Implement secure Wi-Fi, wired and VPN access using RADIUS and certificate-based methods. Define who connects, when and under what conditions… Read More
Single Sign-On (SSO)
Enable secure, one-click Single Sign-On (SSO) for SAML 2.0-based applications with integration support for Okta, Ping and Microsoft AD… Read More
Two-Factor Authentication (2FA)
Strengthen login security with OTP-based or authenticator app-based 2FA for admin, users and guest logins… Read More

Policy Enforcement Engine
Define detailed access policies based on roles, device types, posture status, location, time of day and more. Apply dynamic VLANs or deny access instantly… Read More
Adaptive Authentication
Automatically adjust authentication strength based on user behaviour or access context such as location, device risk or unusual login attempts… Read More
BYOD and IoT Control
Allow users to register personal devices with posture checks and certificate provisioning with no IT intervention required.
IoT devices can connect securely without compromising the network. Control what they can access using identity or MAC-based profiling… Read More
Device Profiling & Posture
Detect, organize and monitor devices using methods like NMAP, SNMP, MAC OUI and QAM Posture Agent. Know what’s connected and its compliance state in real-time… Read More
Passwordless Access with X.509 Certificates
Issue and manage X.509 certificates for passwordless Wi-Fi, wired and VPN access. Fully integrated PKI or connect to an external CA… Read More

Guest Access & Captive Portal
Create branded guest onboarding portals with customizable workflows, OTP delivery, sponsor approval and usage limits. Enable self-service check-ins for visitors… Read More
Real-Time Analytics & Logs
Get visibility into access events, device behavior, failed attempts and posture changes. Export logs or forward them to external SIEMs for auditing… Read More
Multi-Vendor Network Integration
Supports multi-vendor networks across wired, wireless and VPN setups. Integrates with NAC systems, firewalls and UEM tools for extended control… Read More

Syslog, Backup & Restore
Track your logs via Syslog and maintain operational continuity with automated backup and restore options… Read More
Authentication & Authorization
AAA Authentication with 802.1x
Centralized Authentication, Authorization and Accounting for Wi-Fi, wired, VPN and web-based access. Smoothly integrates with existing identity infrastructure such as AD, LDAP and SAML.
Single Sign-On (SSO)
Enable secure, one-click Single Sign-On (SSO) for SAML 2.0-based applications with integration support for Okta, Ping and Microsoft AD.
Two-Factor Authentication (2FA)
Strengthen login security with OTP-based or authenticator app-based 2FA for admin, users and guest logins.
Policy & Access Management
Policy Enforcement Engine
Define detailed access policies based on roles, device types, posture status, location, time of day and more. Apply dynamic VLANs or deny access instantly.
Adaptive Authentication
Automatically adjust authentication strength based on user behaviour or access context such as location, device risk or unusual login attempts.
BYOD and IoT Control
Allow users to register personal devices with posture checks and certificate provisioning with no IT intervention required.
Device Management & Security
Device Profiling & Posture
Detect, organize and monitor devices using methods like NMAP, SNMP, MAC OUI and QAM Posture Agent. Know what’s connected and its compliance state in real-time.

Passwordless Access with X.509 Certificates
Issue and manage X.509 certificates for passwordless Wi-Fi, wired and VPN access. Fully integrated PKI or connect to an external CA.
Guest Access & Onboarding

Guest Access & Captive Portal
Create branded guest onboarding portals with customizable workflows, OTP delivery, sponsor approval and usage limits. Enable self-service check-ins for visitors.
Security & Control Features
Analytics & Integration
Real-Time Analytics & Logs
Get visibility into access events, device behavior, failed attempts and posture changes. Export logs or forward them to external SIEMs for auditing
Multi-Vendor Network Integration
Supports multi-vendor networks across wired, wireless and VPN setups. Integrates with NAC systems, firewalls and UEM tools for extended control
Operational Continuity
Syslog, Backup & Restore
Track your logs via Syslog and maintain operational continuity with automated backup and restore options
Customization & Support
Deployment Options
Managed Cloud Controller
Fully hosted and maintained by Quantum Networks. Ideal for distributed or cloud-first organizations with minimal setup.
Virtual Appliance (On-Prem)
Deployable on VMware, Hyper-V or KVM. Offers complete control over data and integration with internal systems.
Physical Appliances (On-Prem)
Plug-and-play hardware with built-in security for regulated or offline environments.
Device Profiling Methods
NMAP
Scans devices to detect OS, open ports and running services. Useful for identifying rogue or unmanaged systems.
QAM Posture Agent
Get detailed endpoint posture insights including antivirus status, app lists and OS state for real-time policy enforcement.
SNMP
Profiles infrastructure devices like printers, switches and cameras using SNMP polling.
MAC OUI
Detect device manufacturers using MAC OUI to classify unmanaged or IoT devices.
Use Cases
University Campus
Manage Wi-Fi access across multiple campuses with passwordless onboarding, guest access and BYOD registration. No physical infrastructure is required.
Technical Institute
Host QAM as a virtual appliance on-prem to meet data residency rules and integrate with local Active Directory.
Govt & Defence
Deploy QAM as a hardened appliance in air-gapped environments for strict access control and audit-ready compliance.
Corporate Network
Enable SSO, 2FA and posture checks for employee devices while securing IoT devices using SNMP and MAC OUI profiling.
K-12 School
Manage student BYOD access with MAC profiling, assign time-based access and issue guest credentials with SMS OTP.
Retail Chains
Use cloud deployment to manage Wi-Fi access across branches, applying role-based VLANs and monitoring with centralized logs.

