BYOD and IoT Control
- Workplaces these days aren’t just about company laptops and phones. Employees bring their own devices (BYOD: Bring Your Own Device) and offices are filled with IoT gadgets like printers, smart cameras and sensors. While these devices improve flexibility and efficiency, they also create new security risks if not properly managed. That’s where BYOD and IoT Control are useful. These ensure that only safe and trusted devices can connect to your network, without slowing down productivity.
How Does BYOD and IoT Control Work?
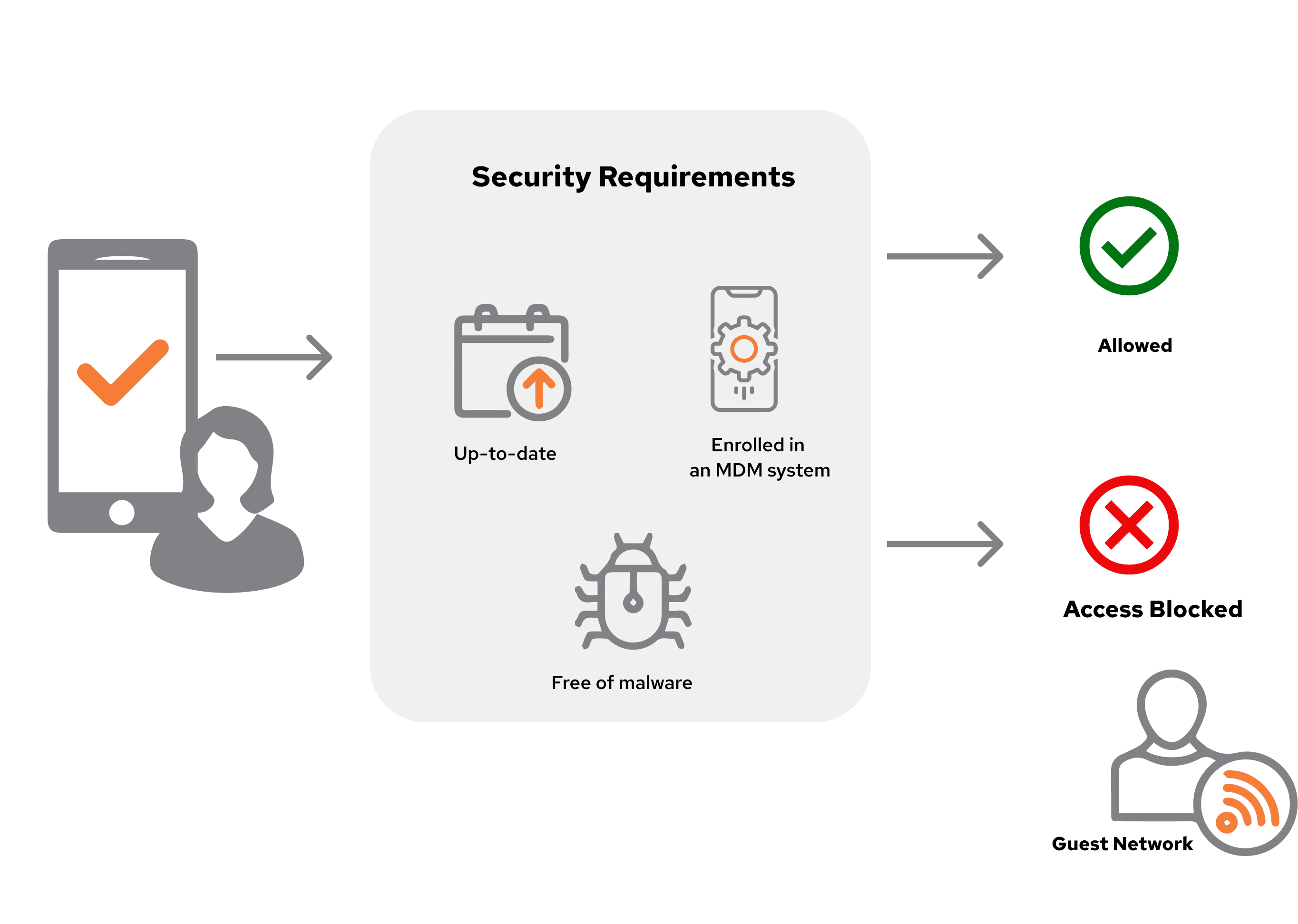
Employee Devices (BYOD)
When an employee brings their personal phone or tablet, the system first checks whether it meets security requirements (like being up-to-date, free of malware or enrolled in an MDM system). If it passes, the device is allowed in. If not, access is blocked or restricted to a guest network.
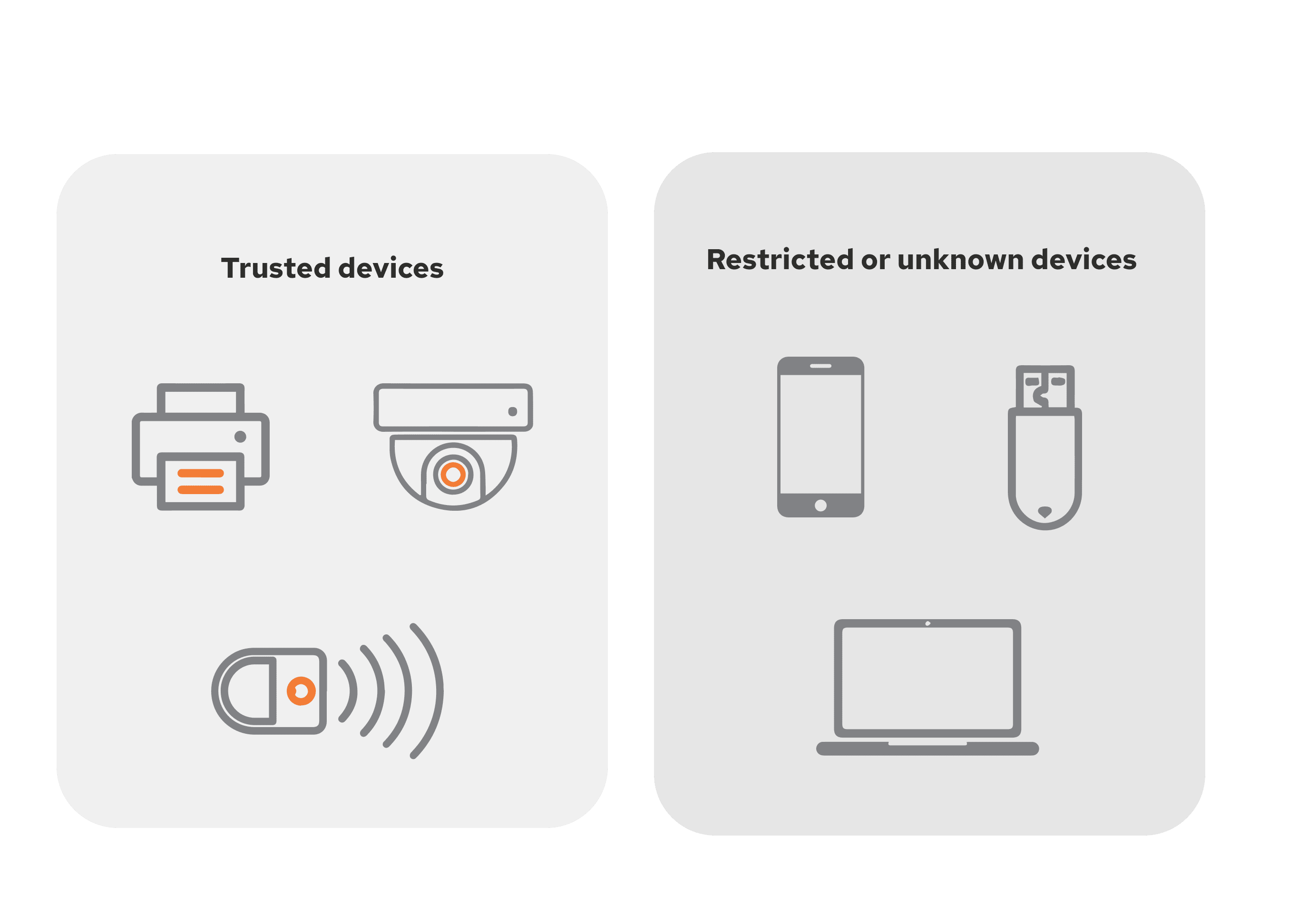
IoT Devices
IoT gadgets (like printers, IP cameras or smart sensors) usually can’t run complex security checks. Instead, the system identifies them by unique device profiles or MAC addresses and places them in controlled network segments. This prevents them from becoming an entry point for hackers.
In short, BYOD and IoT Control create separate “lanes” on your network. Trusted devices in one lane, restricted or unknown devices in another, to keep everything safe and organized.
Why BYOD and IoT Control Matters?
Security First
Stops untrusted devices from becoming security loopholes.
Better Productivity
Employees can safely use personal devices without risking the whole network
IoT Safety
Protects vulnerable IoT gadgets from being exploited.
Network Segmentation
Ensures devices are placed in the right part of the network (e.g. personal devices in guest VLANs, company laptops in secure VLANs).
Visibility for IT Teams
Gives admins a clear view of every device connected, whether it’s an employee’s phone or a smart camera.
BYOD and IoT Control with QAM
- Quantum Access Manager (QAM) makes BYOD and IoT security simple:
Uses 802.1X and MAB (MAC Authentication Bypass) to control both modern and legacy devices.
Creates policies that separate personal, corporate and IoT devices automatically.
.
Integrates with identity providers (like AD, LDAP, Azure) to ensure only authorized users connect.
Provides real-time logs so admins always know what’s on the network.
Adds adaptive and certificate-based authentication for stronger security without extra complexity.
FAQs
What is BYOD?
BYOD stands for Bring Your Own Device. It means employees using their personal devices (like smartphones or laptops) to access company networks or apps.
Why are IoT devices considered risky?
Most IoT gadgets lack advanced security, making them easy targets for hackers if left uncontrolled.
How does QAM handle devices that don’t support 802.1X?
QAM uses MAB (MAC Authentication Bypass) to identify and control such devices safely.
Can employees still use their personal devices freely?
Yes. But QAM ensures personal devices connect securely and often isolates them to guest or limited networks.
Does BYOD and IoT Control affect performance?
No. It improves security without slowing down device connectivity or user experience.